HUBUNGAN ETNIK - Topik Agama Dan Hubungan by Safwan Zakwan on Scribd
Monday, 17 October 2016
Tuesday, 27 September 2016
Wednesday, 7 September 2016
Sunday, 29 May 2016
Tuesday, 3 May 2016
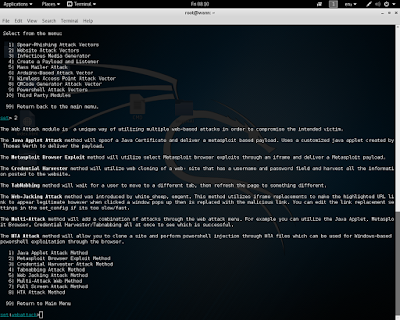
PENETRATION TESTING
Earlier we conducted a scan of a target and discovered several services open.
command
nmap -p 0-65535 [ip target]
nmap -sV -p [target port] [ip target]
Moving over to our metasploit console check to see if the exploit has been entered
command
search samba smbdTo use the exploit we type the command “use” followed by the name of the exploit. This loads the exploit into our metasploit platform. By typing “show options” see what type of settings I need to set before launching this exploit.
To do that we type "set RHOST” followed by the IP address and then we check our options again to verify the settings are correct.
comand
use
show options
set RHOST
set RHOST
useradd -m [username]
passwd [userpass]
password [root]
re-type password [root]
NEXT page.
Friday, 22 April 2016
SECURE YOUR FILE USING AxCrypt
This tools help encrypt the file to secure the confidentially and integrity of the file from unauthorized person.
STEP 1 : Choose any confidential file to encrypt. AxCrypt also can
encrypt many file at the same time if the files are in the same folder.
STEP 2 : Right click on the file or folder that want to encrypt > select AxCrypt from the menu > select Encrypt to encrypt those selected file/folder.

STEP 3 : Create a passphrase to secure the file. Try create a strong
passphrase by creating a long and mix with symbols, number, capital
letters and etc. The stronger the passphrase, the stronger the
encryption.

STEP 4 : After the encryption, the file icon will change to the AxCrypt shield. It also will change the file extension to .axx.

STEP 5 : When you try to open the encrypted file, it will ask you the
passphrase. So you need to remember the passphrase to use the file
again. After you edit the file, it will automatically encrypt the
changes. Do not tick the check box says “Remember this decryption” so
that only an authorized person that have the passphrase only can open
the file.
# If you no longer want to keep this file as an encrypted file, right-click on the file and select Decrypt at the menu so it will permanently change it back to normal file.

Sunday, 17 April 2016
MD5 HASH
APPLICATION : IgorWare Hasher
STEP 1 . CREATE FILE.TXT IN NEW FOLDER
STEP 2 . OPEN APPLICATION TOOL
STEP 3 . CLICK BROWSE BUTTON TO OPEN FILE.TXT
WHAT IS MD5 HASH
MD5 which stands for Message Digest algorithm 5 is a widely used cryptographic hash.The idea behind this algorithm is to take up a random data (text or binary) as an input and generate a fixed size “hash value” as the output. The input data can be of any size or length, but the output “hash value” size is always fixed. Here is an example of MD5 Hash function at work:
REFERENCE
http://www.md5.net/